The maritime industry is facing the problem of cyber threats, like every other global industry. As vessels become increasingly connected to the internet, the risks have grown exponentially in a very short period.
For vessel charterers who depend on a broad range of practices and policies related to managing organizational data and communications, the risks have increased exponentially.
Activities such as email communications, document sharing permissions, versioning, information security, and the exchange of sensitive data or competitor information are called “information governance” and cover a broad range of practices and policies related to managing organizational data and communications.
By implementing robust information governance practices, organizations can effectively manage, secure, and derive value from their data assets while minimizing risks and ensuring compliance with relevant regulations.
One solution to increasing data security is to leverage dedicated software platforms that incorporate comprehensive security measures. However, it is important to remember that this approach must extend beyond simply a software platform. We must match and surpass the capabilities of cybercriminals who are armed with an arsenal of sophisticated techniques, and seek to exploit maritime vulnerabilities in both onboard and onshore operations.
The Evolution of Maritime Connectivity: From Dial-Up to Starlink
Today’s vessels are floating data centers, constantly connected to the internet and vulnerable to cyber threats.
But this connectivity is relatively new. The evolution of maritime connectivity has been rapid – and revolutionary:
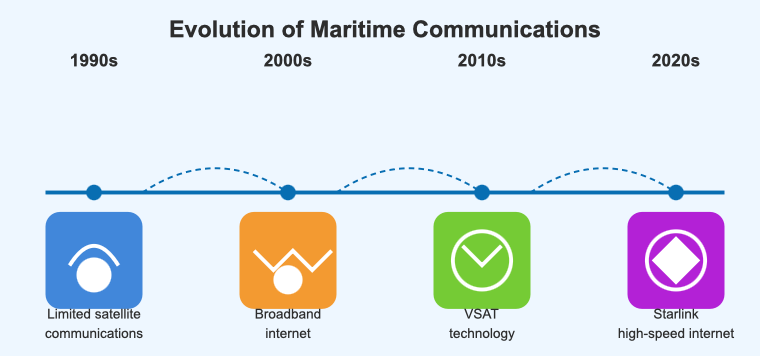
According to Thetius, a leading maritime innovation and technology research firm, the very thing that makes modern shipping operations efficient—constant connectivity—also makes them the most vulnerable.
This is especially important when the number of connected ships is expected to reach 75,000 by 2026, up from 50,000 in 2021.
That’s a 50% increase in just five years of data being exchanged over insecure channels, primarily email. Every email sent is a potential entry point for a cyberattack. In an industry where timing and accuracy are everything, the repercussions can be catastrophic.
The main issue is that most maritime internet systems were not necessarily designed with cybersecurity in mind. Every connected device, from navigation systems to crew smartphones, is a potential gateway for cybercriminals.
Common Cybersecurity Threats in the Maritime Sector
Some of the most concerning cyberattacks include:
– Phishing Attacks: Cybercriminals send deceptive emails to trick recipients into divulging sensitive information or clicking on malicious links. In 2023, 60% of maritime companies reported phishing attempts. This recently happened in Australia in November 2023: A sophisticated cyberattack crippled DP World’s operations, resulting in significant delays and financial losses.
– Ransomware: Malicious software that locks down systems until a ransom is paid, which can bring shipping operations to a halt. The average ransom demand in the maritime sector reached $3.2 million in 2023. As an example, in July 2023, the Port of Nagoya (Japan’s largest port), was paralyzed, disrupting the flow of goods and causing widespread chaos.
– GPS Spoofing and Jamming: Interfering with a ship’s navigation system, potentially leading it off course, which is particularly dangerous in congested or sensitive waters. In a particularly alarming case in June 2017, over 20 ships in the Black Sea reported that their GPS systems showed their location as being 32 kilometers inland at an airport, despite being at sea.
– Malware: These dangerous bits of code are stowaways in your systems, causing havoc when you least expect it.
The question is, how can charterers, who are already overwhelmed with paperwork and emails, safeguard their operations?
Best Practices for Dealing with Maritime Cyber Threats
To effectively combat such malicious activities, organizations must adopt a comprehensive approach to cybersecurity.
This means not only implementing cutting-edge technological solutions but also fostering a culture of security awareness among all personnel. By leveraging a wide array of tools, methods, and best practices, maritime companies can significantly enhance their resilience against cyberattacks.
Cybersecurity Training
Training is essential for ensuring that crew members are well-prepared and informed. Everyone understands the value of training, and the importance of maintaining a baseline of knowledge among employees.
However, it’s important to strike the right balance. Overtraining can lead to diminished effectiveness, as crew members may become less vigilant over time—a phenomenon often referred to as “training fatigue.”
Foster a culture of continuous learning by prioritizing quality over quantity.
IMO Guidelines and the Importance of Safeguarding Data
The International Maritime Organization (IMO) has recognized the growing threat of cyberattacks and has issued guidelines to help the industry safeguard against these risks.
These guidelines, outlined in Resolution MSC.428(98) and complemented by MSC-FAL.1/Circ.3, provide a framework for incorporating cyber risk management into existing safety management systems (SMS) as defined by the International Safety Management (ISM) Code.
These guidelines emphasize a risk-based approach to maritime cybersecurity, focusing on five functional elements: identify, protect, detect, respond, and recover.
Shipowners and operators are required to assess their cyber risks, implement appropriate safeguards, develop capabilities to detect cyber events, create response plans, and establish processes to restore systems affected by cyber incidents.
These guidelines apply to all vessels and have become mandatory as of January 1, 2021.
To support implementation, the IMO encourages the use of industry-developed guidelines, such as those created by BIMCO and other organizations. These supplementary resources provide more detailed, practical advice on developing and executing cyber risk management strategies.
Managing your Operations on a Dedicated, Secure Platform
Enter the solution: secure, dedicated software platforms for the various requirements you have on board.
Dedicated platforms can offer multiple advantages:
– Secured and Encrypted Data: All data exchanged on the platform is encrypted, reducing the risk of interception or tampering.
– Secure Messaging: Communication within the platform is secure, with diminished risk of phishing attacks or unauthorized access.
– No Outside Providers: By keeping everything within a closed ecosystem, a platform can eliminate the risk of third-party vulnerabilities.
– Common Pitfalls are Avoided: Issues like obsolete operating systems, outdated antivirus software, and inadequate access controls are mitigated when using a dedicated platform.
A dedicated platform can significantly reduce manual paperwork – and the associated mistakes. Automation and digital workflows not only streamline operations but also reduce the likelihood of human error. With a user-friendly, secure system, you spend less on cybersecurity training.
This, in turn, leads to more efficient operations.
[TIP] SOC2 Compliance
Many maritime SaaS companies have implemented Service Organization Control Type 2 (SOC 2), a cybersecurity compliance framework developed by the American Institute of Certified Public Accountants (AICPA).
The primary purpose of SOC 2 is to ensure that third-party service providers store and process client data securely. It focuses on five “trust service principles”—security, availability, processing integrity, confidentiality, and privacy. It’s a critical framework for organizations that handle sensitive data.
Voyager Portal is SOC 2 compliant, demonstrating our commitment to robust data protection and information security practices. Our best practices include regular code review, security assessment, and integration at every stage of our development life cycle. We work proactively to deal with potential vulnerabilities before they become threats.
These are some of the actions that we regularly employ to maintain our SOC 2 Type II Certification, a testament to our commitment to ensuring that client data is protected with the best internal processes.
SOC 2 compliance provides independent verification that we have implemented stringent controls to safeguard customer data, ensuring confidentiality, integrity, and availability of information and provides the assurance that we adhere to industry-recoIN gnized standards for managing and protecting sensitive information.
>> Learn more about our certification process and security measures.
Conclusion
In the rapidly changing landscape of cybersecurity, the maritime industry faces significant threats from cybercriminals employing diverse and sophisticated tactics.
To effectively counter these attacks, organizations must adopt a comprehensive approach that includes advanced technological solutions and a strong culture of security awareness among personnel.
Ultimately, the key to success lies in matching and surpassing cybercriminals’ capabilities. Only by employing a diverse and adaptive set of defensive measures can organizations hope to stay one step ahead in the critical battle for digital security.


